Review your page vulnerabilities
This report has different information than the low volume page report
Vulnerabilities are flaws that can be exploited by an attacker to compromise a system. Vulnerabilities are continuously being discovered for widely used web assets such as jQuery and Bootstrap. These are assets you may use in your Engaging Networks templates or on pages in code blocks. The scan results page report will show pages that have assets with known vulnerabilities and the severity of the vulnerabilities so they can be updated or removed from your pages.
How to access the report
The report is available to Super Admins from the Security Center under Hello > Security Center > Review your page vulnerabilities. There is also a template version of the report which is currently only accessible via a URL.
Available information
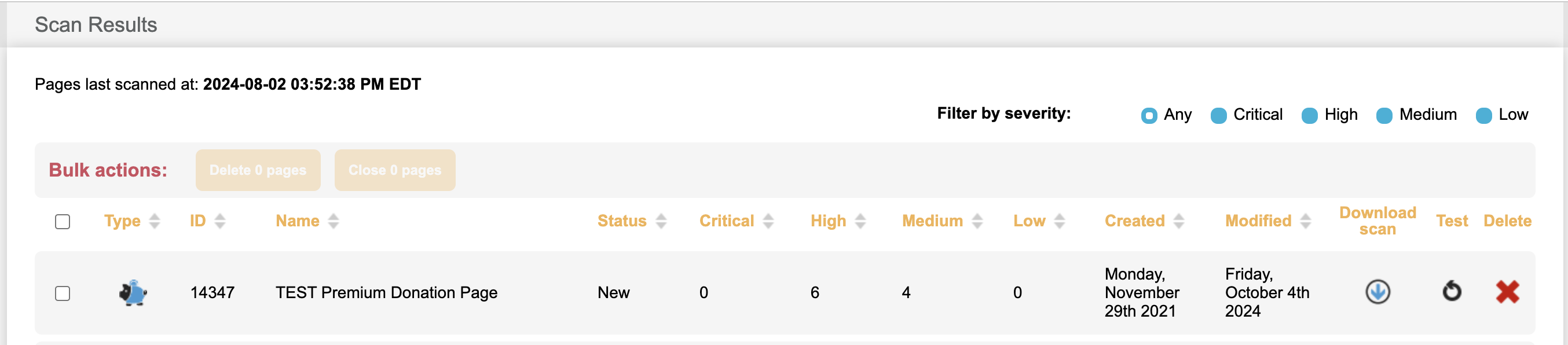
The main dashboard displays any pages where payments can be taken with known vulnerabilities, the status of the pages, number of vulnerabilities listed by severity (critical, high, medium, and low). You can also download the results of that scan, test pages and delete pages or bulk close or delete pages.
Scans are not updated in real time. A snapshot of the pages is taken on Monday and Thursday mornings to be scanned and the report is updated by the end of the day on Tuesdays and Fridays. Changes made after the snapshots will not be reflected until the following scan.
Severity | Definition | Required Action |
|---|---|---|
Critical | Vulnerabilities classified as Critical represent the most severe security risks. Exploitation of these vulnerabilities often leads to a complete system compromise, including full access to sensitive data, complete control over the system, or severe service disruptions. | Immediate action is required, as these vulnerabilities can cause catastrophic damage if exploited. They might allow remote code execution, full system access, or the spread of malware across networks. |
High | High level vulnerabilities pose significant security risks and, if exploited, can lead to substantial damage or loss. They often require user interaction or specific conditions to be met for exploitation. | These vulnerabilities can lead to unauthorized access, data leaks, or service disruptions, and they typically require prompt remediation to avoid exploitation. |
Medium | Medium level vulnerabilities present a moderate risk. They may require more complex conditions or specific knowledge to exploit, and their impact is generally less severe than high-level vulnerabilities. | If exploited, these vulnerabilities can lead to partial system compromise, data exposure, or limited functionality loss. They should be addressed, but they may not require immediate action. |
Low | Low level vulnerabilities pose minimal risk and are typically difficult to exploit. Their impact is usually limited, and they might require highly specific conditions to be harmful. | These vulnerabilities are unlikely to lead to significant damage or compromise. They should be addressed as part of routine maintenance but are generally not urgent. |
Downloading and reviewing scans
Select the
 icon in the Download scan column to download the scan for a page with vulnerabilities
icon in the Download scan column to download the scan for a page with vulnerabilitiesThat will produce an HTML file with information including the specific asset that has vulnerabilities, the file path of the asset, and information on what is vulnerable about the asset.
Using that information, you can find the vulnerable asset in your page template or on your page in a code block and update it to non vulnerable version (or remove it entirely). This resource details how to make these updates.
This task may require help from a web developer or someone comfortable with HTML. Note that making changes to assets could change the functionality of your pages. Be sure to test any updated code on a duplicated version of your page before making changes to any live pages being accessed by your supporters.
How to bulk close and redirect pages
Select the page/s you would like to close and redirect by checking the box next to the name of the forms
To close and redirect, click the
 button next to Bulk Actions and the options to redirect will pop up
button next to Bulk Actions and the options to redirect will pop upSelect where to want to redirect to: a closed page (webpage), another page (another Engaging Networks page), or an external URL
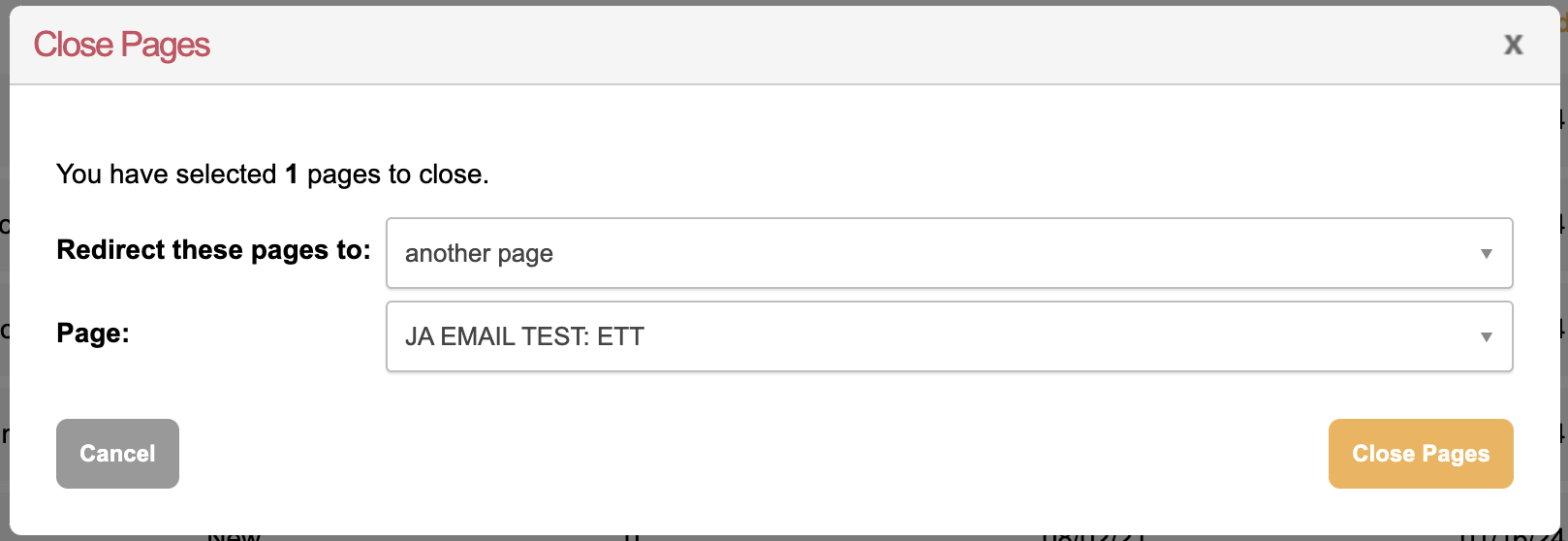
Then select which page or paste in the URL and click Close Pages
Closing or deleting pages will not cause recurring transactions to stop processing.
How to bulk delete pages
Select the page/s you would like to delete by checking the box next to the name of the form
To delete just select
 button next to Bulk Actions (there is a confirmation step following this)
button next to Bulk Actions (there is a confirmation step following this)Confirm the pages should be deleted by selecting Delete
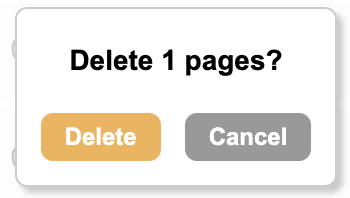
Pages cannot be restored after deleting. Be sure you’re only selecting pages that you want to entirely delete from your Engaging Networks account. Deleted pages will not be available to query on in query builder.
